Side-Channel Security
Project Overview
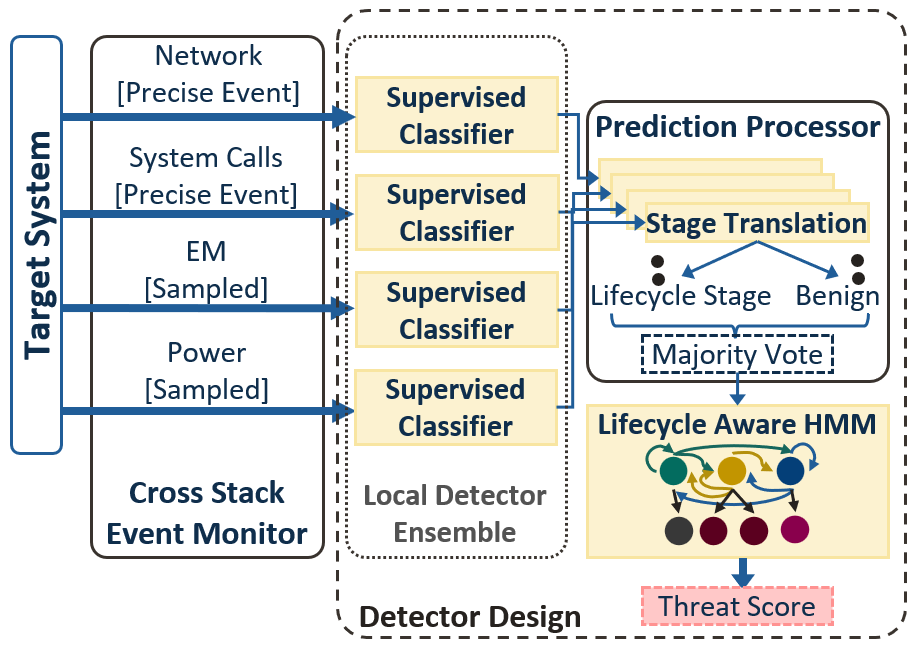
Information leakage through physical side channels, such as electromagnetic (EM) emissions or power consumption, has been exploited by attackers to exfiltrate data and compromise computer systems. However, side channels can also be leveraged defensively. By characterizing a system during normal operation, side channel-based malware detectors can identify anomalous behavior. These out-of-band detectors offer significant advantages over traditional in-band software-based detection methods. Because they operate externally, a compromised application or operating system (OS) cannot undermine the detector. Moreover, these detectors are non-intrusive, requiring no modifications to existing hardware or software, even as new attack vectors emerge. These features are particularly critical for embedded systems, which are often resource-constrained, have long lifetimes, and typically lack in-field update capabilities.
This project explores side-channel security from both an attack and defense perspective. On the attack side, we investigate novel methods to analyze and exploit vulnerabilities of embedded computer systems up to the software level. We particularly focus on the EM side-channel, which offers rich temporal and spatial information that expands the attack surface and thus provides unique challenges and opportunities in predicting vulnerabilities and extracting new types of information. On the defense side, we explore methods to improve behavioral malware detectors with a focus on power side-channels and other computer system signals. In particular, side-channel detection that mainly focuses on the execution phase of attacks often performs poorly in the presence of complex systems with noisy baseline behavior and potentially stealthy attacks. In practice, real-world exploits involve multiple distinct phases designed to prime and deliver an exploit and afterwards maximize post-execution persistence and reward. Lifecycle-aware (LA) detection leverages this contextual knowledge to improve detection confidence by correlating individual anomalies within the broader logic of a complete attack sequence, rather than in isolation. Our work proposed a novel ensemble-based power detector and benefits of power-based LA detectors to better secure complex multicore embedded systems. More recently, we are investigating the generalizability of lifecycle awareness by developing a multivariate LA detector that monitored hardware performance counters (HPCs), system calls, and network captures to secure network-connected servers.
Releases
Selected Publications
-
Alexander Cathis, Mulong Luo, Mohit Tiwari, and Andreas Gerstlauer, "LAPD: Lifecycle-Aware Power-Based Malware Detection," IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, CA, May 2025.
[
 pdf]
pdf]
-
Alexander Cathis, Ge Li, Shijia Wei, Michael Orshansky, Mohit Tiwari, and Andreas Gerstlauer, "SoK Paper: Power Side-Channel Malware Detection," International Workshop on Hardware and Architectural Support for Security and Privacy (HASP), Austin, TX, November 2024. (Best paper award)
[
 pdf]
pdf]
-
Vishnuvardhan V. Iyer, Aditya Thimmaiah, Michael Orshansky, Andreas Gerstlauer, and Ali E. Yilmaz, "A Hierarchical Classification Method for High-Accuracy Instruction Disassembly with Near-Field EM Measurements," ACM Transactions on Embedded Computing Systems (TECS), vol. 23, no. 1, pp. 10:1-10:21, January 2024.
[
 pdf]
pdf]
-
Aditya Thimmaiah, Vishnuvardhan V. Iyer, Andreas Gerstlauer, and Michael Orshansky, "High-Level Simulation of Embedded Software Vulnerabilities to EM Side-Channel Attacks," International Conference on Embedded Computer Systems: Architectures, Modeling and Simulation (SAMOS), Samos, Greece, July 2022.
[
 pdf]
pdf]
